Welcome to Industry 4.0
With IIoT and the concept of smart machines, a new form of the industrial revolution has begun. Experts name it Industry 4.0. The Third Industrial Revolution started in the 1950s, where we began incorporating electronics into machinery. After the 1990s, we incorporated computers into machines for data acquisition and better control.
The Fourth Industrial Revolution or Industry 4.0 is all about turning these computer-operated machines smart. This integration leads to smarter factories where machines communicate with each other and monitor the performance itself. IIoT is the cornerstone for industry 4.0 because this level of cross-communication was not possible before the introduction of smart digital devices.
Today, an operator can monitor the machine from a smart phone, tablet or laptop and is aware of every single detail without being present in the same room. If the machine sense something that is out of its operating boundary, it will duly alert the monitoring system including the personnel operating the machine.
By incorporation communication and interlinking between machines, Industry 4.0 brings a cohesive approach to the manufacturing/production floor, unlocking better productivity and profitability in the process.
Challenges and Cybersecurity in IIoT
Currently, IIoT faces two significant challenges – the lack of security and disparate older communication protocols and the incompatibility with newer internet communication protocol.
IIoT with an internet based protocol has certain built-in security and can vary from a simple defense again network viral attack to very hardened access prevention to guard against malicious attacks from inside and outside an organization. The challenge has always been with the older and disparate protocols that can’t directly be translated to the new internet based protocols when adopting an IIoT implementation. Fortunately, those risks can be mitigated with a hybrid implementation of both the legacy and newer equipment. On premise physical security for older equipment with lock down access and secure remote access to newer equipment with advance robust security is an excellent way to transition to a digital world and access to machine insights as never before, anytime, anywhere.
Going digital with IIoT and remote access might sound scary at first, but the fact is, a digital world is also a world that can adapt quickly to changes and updates to enhance security and improve operability. Staying with older existing equipment that can’t easily be updated will eventually result in higher operating cost in maintenance and compromised security that can result in severe equipment downtime and monetary lost. Today a cybersecurity break-in can hold a factory or organization hostage, bringing the factory or operation to a halt in exchange for monetary value.
Introduction to IIoT Security
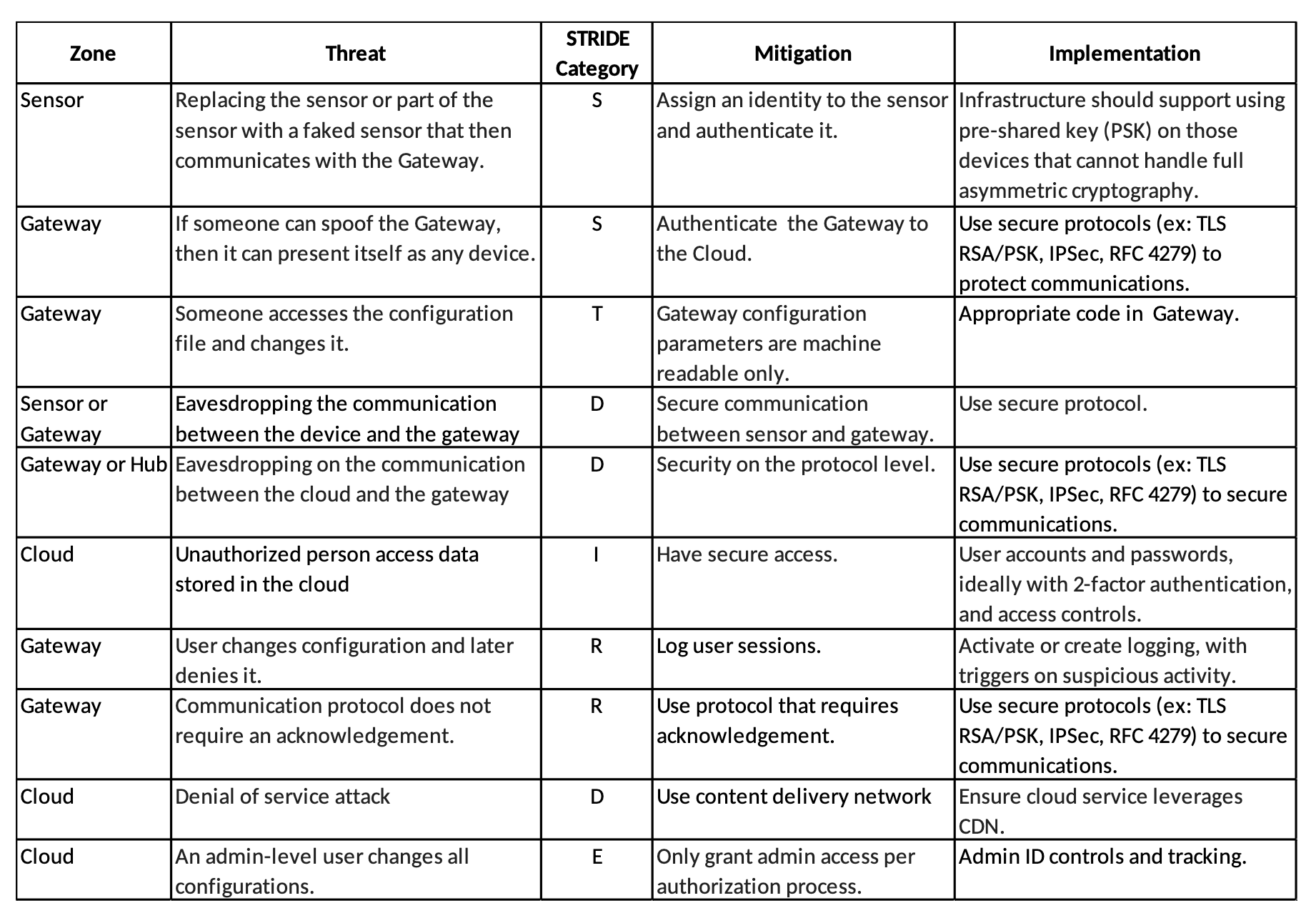
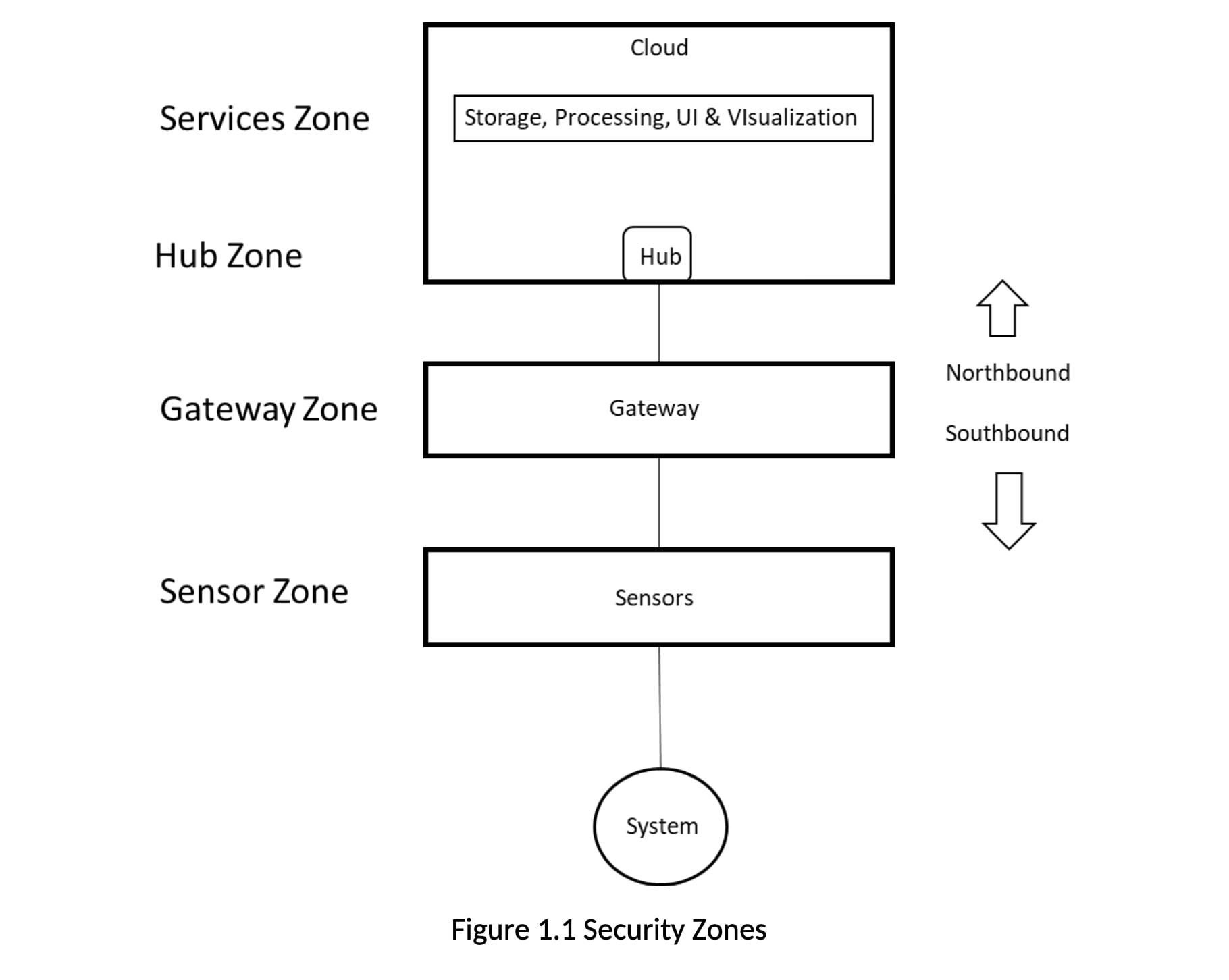
IIoT solutions must be trusted to provide data and information with integrity, as they are monitoring and measuring business critical systems and environments. That trust is verified by ensuring the system is secure against threats. Threat modeling is the best approach to designing for security. Using a typical IIoT solution configuration, we can identify several zones (Figure 1.0). The boundaries of these zones are where data and information transition from one solution element to another. Threats will be against the boundaries of these zones.
For the threat analysis we use the STRIDE model, which defines threats using the categories in the table below.
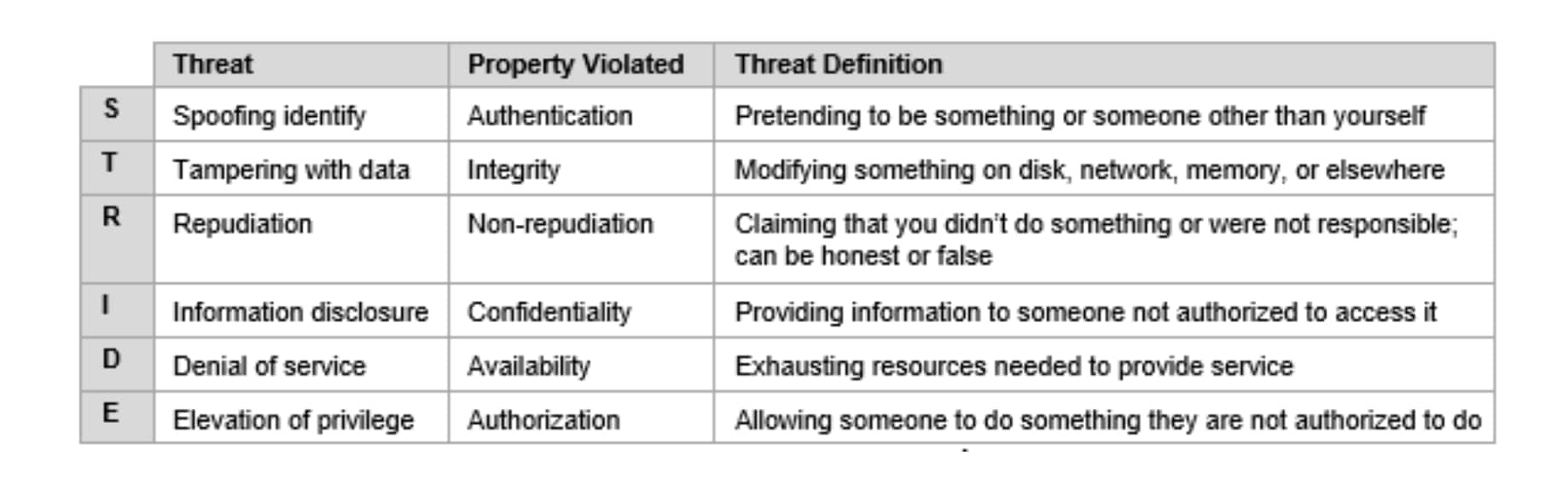
Applying the STRIDE model to the security zones identified above, we can generate a table similar to the one below. This is a simplified version of a much longer table that shows the security zone, the type of threat against it, and how that threat could be mitigated.